Purpose:
As I mentioned yesterday here is the next five levels solved using only python. No walkthroughs were used or references for OverTheWire. Instead all information was from python documentation and other discussion posts relating to python. This has helped me understand the material deeper. Some of the details will be left out considering most of it was covered in original discussion posted several months back. I want this post to focus more on the python side of things.
NOTE: The filenames do not match the level description. Mainly because I believe I started at level 1 instead of 0. All files are 1 ahead of the other.
Level 6
To start off level 6 we notice we have a form to submit a secret. Nothing really to take away here other then the fact that the names we will post to later will be secret and submit.

To get a better undertanding of what is going on behind the scenes we will look at the source code provided by visiting index-source.html.
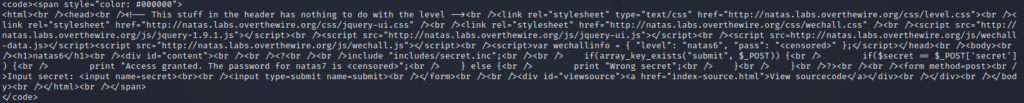
The source code is harder to read in the terminal. I do believe this can be fixed with sublime text (I plan to try in the future). This time around I took advantage of a fantastic website to do the work for me (htmled.it)
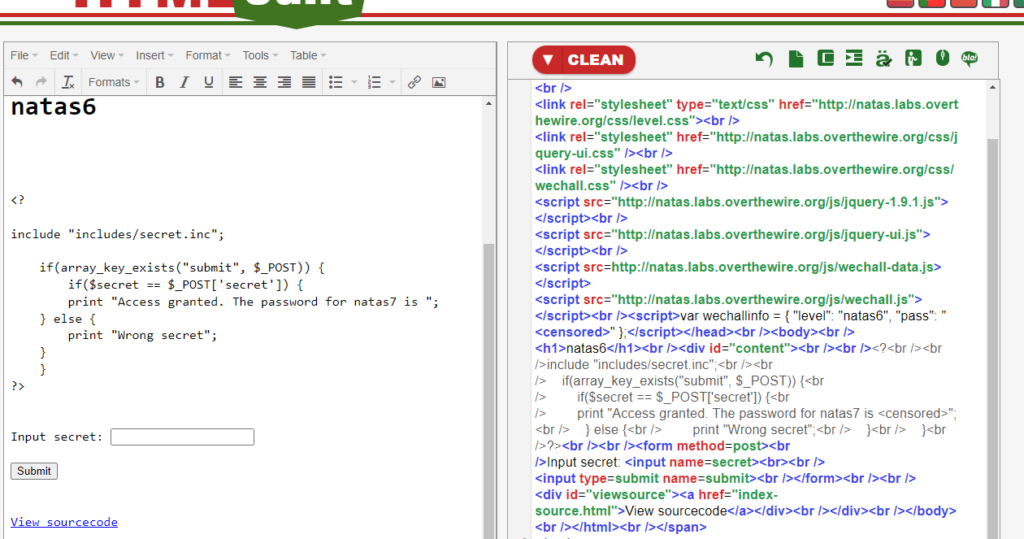
Now that we can see it more clearly we first notice a directory includes/secret.inc. We then see how the form works. It appears that when we post ‘secret‘ it will compare the PHP variable stored inside secret.inc to the string we posted. If the two match then we will be granted access otherwise we will be denied. Lets go ahead and look at that directory and see what we find.

Easy enough! Knowing the stored secret variable all we need to do is copy and paste this into the form.
To make it easier to read I created another variable key. This key variable will store the secret we copied. We can then plug this into our dictionary inside the post function.
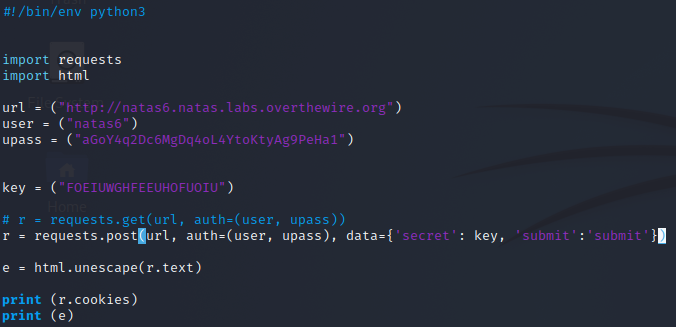

Level 7
For level 7 we notice two links upon viewing the page. About and Home. We also have a hint, “password for webuser natas8 is in /etc/natas_webpass/natas8.

Well lets try to traverse to that directory directly in the url.

After printing this request we will see the password for Natas8.

Level 8
Natas8 is similar to the to the last two levels. The biggest difference here being that we have an encoded secret. Once we post a string into the form, the encodeSecret function is called. This will then encode our string and compare the two. If we have a match we will be granted access, otherwise we will be denied access.
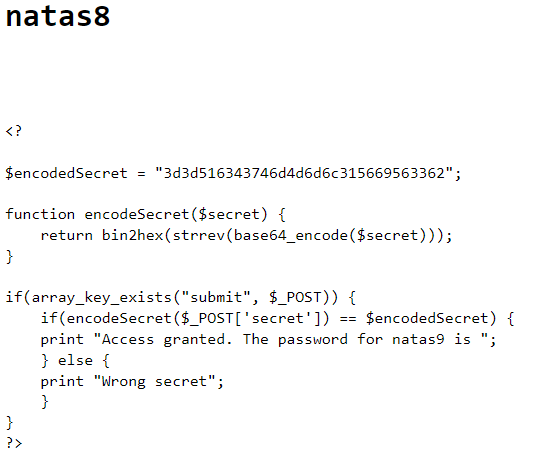
The encodedSecret is the stored string that we must convert. Luckily for us we also have the function that encodes the secret. This means that we can go ahead and reverse engineer the encryption method used. If we take a look inside the function encodeSecret we will see a $secret passed as an argument. This argument gets posted from the form which is our entry. It will then return the encoded secret by first encoding it in base64 then reversing the string and lastly using the PHP function bin2hex.
What we did last time in the original post was create a PHP file and just do these in reverse order. Since we are doing it in python I went ahead and read the documentation until I came up with my own function to perform all three.
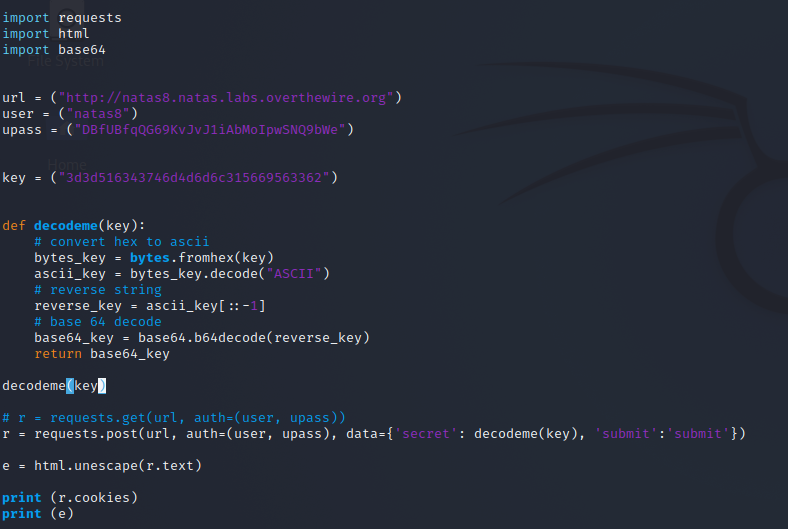
As you can see in the decodeme function I have reversed the encryption by using several builtin modules, bytes.fromhex, .decode(“ASCII”), [::-1] for reversing the string and lastly base64.b64decode(). Once the key has been through each of the steps it is then returned. Returning the value allows us to use it in our post method as shown above.

Level 9
In level 9 instead of reversing a secret we will use remote code execution to gain access to a file and read the stored password itself.
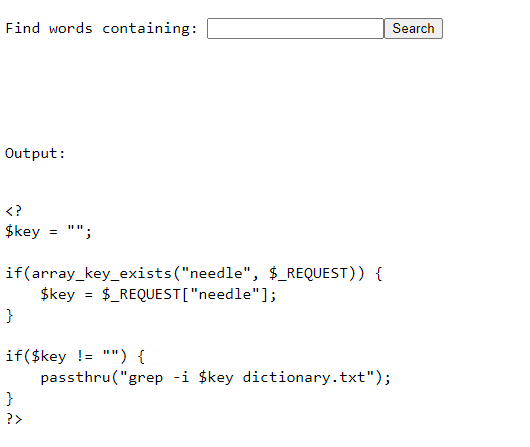
As we can see in the source code we are using the PHP passthru function to grep a character, looking inside of dictionary.txt. As we learned last time the passthru function does allow code execution. So all we have to do again is just exit the current command with ; and run another command. In this particular instance we will traverse to the known path for storing natas_webpass.


Level 10
This time around the company has patched there web application. Preventing us from executing another line of bash by validating input.
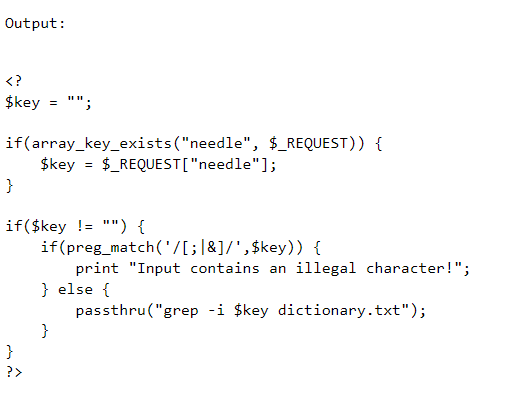
Although they blocked us, we also notice grep is still being used. With grep we are able to look for patterns in multiple files. So not only will we search for a character in the dictionary.txt file, but we will also take a look in the natas_webpass directory.


Conclusion
This was a lot of fun. I was able to learn a lot, it has also gave me more ideas as to what I want to do outside of this excercise. For example when I was researching I learned about pythons library Beautiful Soup. Beautiful Soup can be used to scrape websites. Maybe instead of my current RSS feed I can create my own within Python!
I am unsure of my next project but I do know I will be back to complete NATAS in Python. Until next time, Never Stop Learning!
