Recently as discussed in my last write up I have started a Minecraft Server. Not only did I want to do this for the game aspect but I felt there was a lot of learning that can be had with managing a server. I would say I have a decent base understanding of Linux so this would only help strengthen that knowledge.
This server is hosted in a virtual environment within ESXI. After two weeks of booting up ESXI every time to perform small tasks I thought why not just use SSH.
So with that being said, todays discussion will cover how to install and configure an OpenSSH server and allowing a windows machine to connect.
Disclaimer: Please understand that the keys and information I display is not used in my “production” environment. Only created for practice in my lab.
Requirements:
1. Linux/Windows OS installed
2. Powershell/Putty installed
Lets go ahead and get to it! First we are going to start with installing openssh-server if not already done. This is what will be later configured allowing our Windows machine to SSH into. For those not familiar with SSH I suggest do some reading here. Long story short it will allow a secure session to be created between the two machines giving full access to the terminal.
After installing openssh-server some files will automatically be created. The file that we will care most about is located at /etc/ssh/sshd_config. Before making any modifications I highly suggest creating a backup. This way when your playing around you do not have to worry about making an irreversible mistake.
In addition to making a backup as seen above, I suggest changing the port number to anything other then 22. The default port used is 22. If this were connected to the internet and port was forwarded attackers will be able to quickly scan and determine what service is opened and tailor their efforts towards this service. You can change this port within this sshd_config file.
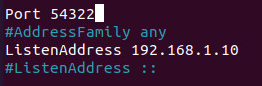
You will also need to specify the ListenAddress. This will be the IP of machine. You can figure this out by using ifconfig.
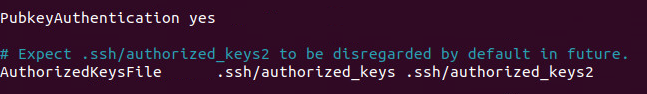
Since we already are in the file editing the port/IP lets go ahead and change two more settings. Lets allow PublicKeyAuthentication. By default this line will be commented out with a #. Just remove the # and change the no to a yes. We also must verify/uncomment the AuthorizedKeysFile. This will be better explained later but is used to tell openssh what public key to accept when the windows machine is attempting authentication.
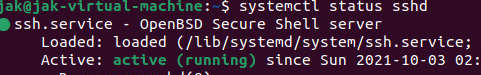
Before going any further I also suggest verifying that the SSHD service is running. With the systemctl status sshd command we are able to see exactly that. Later we will use this a few times in order to restart the service. systemctl restart sshd after applying changes to the configuration file.
Next we will hop over to putty as I found it to be very easy and convenient to generate a key-pair. This can also be done within PowerShell. With installing putty you will get three programs. One of which being Putty Key Generator.
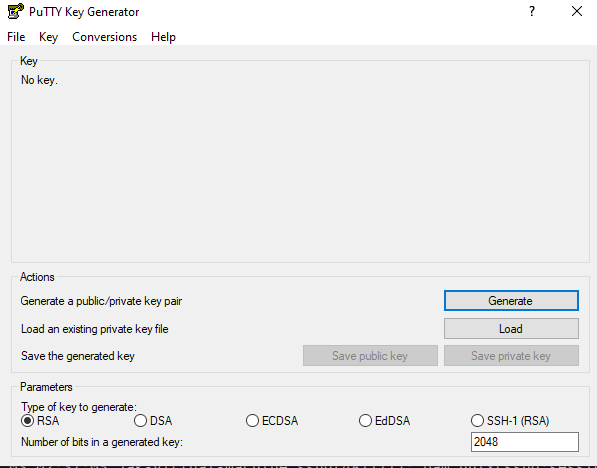
With this application we are able to generate the key. Ensure RSA is selected. Number of bits is your decision, for the purpose of this lab I left it at 2048. 4096 bits is not a bad idea either depending on what you plan on doing. All you have to do next is select Generate. It will then ask you to move the mouse around to randomize the key.
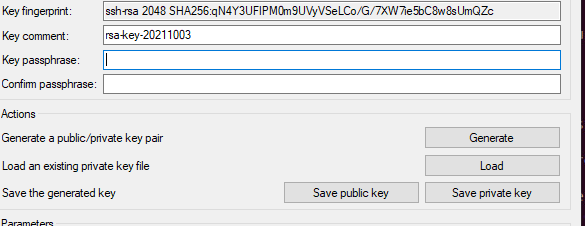
After the key is generated you will receive a hash of the key. This is used to determine if anything has been altered. You also have the option of entering a Key passphrase. For the purpose of this lab I left it blank but it is highly suggested you do so to add that extra level of security. At this point all you have to do is Save Public Key and Save Private Key. You want to save these in the .ssh directory in users home folder on Windows.
Next we will want to transfer the public key from our windows machine to our server. Ever since learning about the simple built in python function I tend to lean that direction. For example on my windows machine within Powershell (after installing python) I ran the following command:
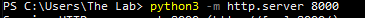
With this running I can then go on my server boot up Firefox and download the key by visiting my local IP:port.
We are almost done! What I forgot to mention is that the key just generated/downloaded is not in OpenSSH format. If you do not follow the steps ahead you may spend several hours trying to figure out why you can authenticate with a password but not a key.
There are two ways to go about this.
1.
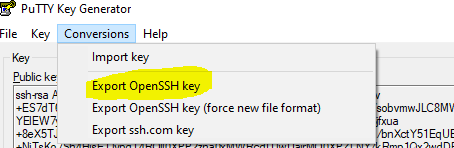
With the first method you can actually just Export an OpenSSH key right after generating. This will then save a seperate key that you can download on the server.
2.
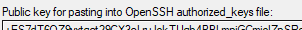
The second method is also fairly easy. After generating the key this will be at the top. You can just copy this key and SSH into the linux server to paste in the authorized_keys file we are about to discuss.
The only thing we have to do next is create the authorized_keys file if not already created and edit some permissions for the file and folder its under. The folder should be automatically created after installing SSH on the Linux machine. It is a hidden folder as you can tell by the directory name .ssh and is in the home directory. An easy way to get back to the home directory within linux is cd ~. After running the ~ you will be in home directory. You can then view hidden directories by using ls -la.
Now we want to ensure the correct permissions are set for the .ssh directory. I would suggest learning about the linux permissions but for the purpose of this writeup we need it set to 700
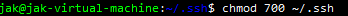
We then want to move into the .ssh directory. Once inside we want to create the authorized_keys file. You can do this by using the touch command. After creating we want to set these permissions to 600.
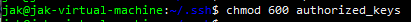
This is where you will copy and paste that key from earlier or you can also append from the key you downloaded. For instance you can do something like this|
cat filename >> authorized_keys
This will take everything from the key you downloaded to linux server and append to that file you specified. It is important that after doing so you open the file and verify the correct format and is on one line. If you nano filename you should see it all on one line.
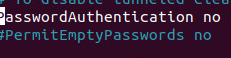
Lastly we want to go back into the sshd_config file and change PasswordAuthentication yes to no
At this point it is just preference on how you want to connect to the server. I first thought I would use putty but then found PowerShell to a better choice for personal preference. If you were to use PowerShell you would use something similar to the following:
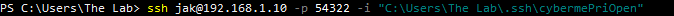
jak will be replaced with the username your logging into via Linux machine. The -p is identifying the port we decided on earlier. Lastly is the -i which will identify the key. This key happen to be the one I downloaded from putty under Conversations > Export OpenSSH Key.
You also have the option of using Putty.
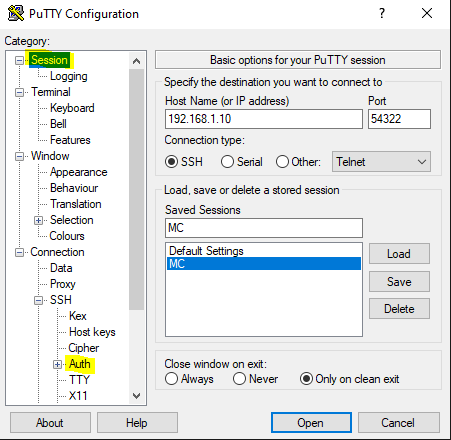
The two tabs you will spend most time in are Session and Auth. Under session you want to enter IP address, Port and connection type.
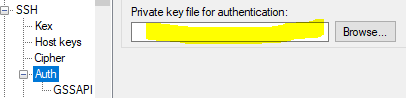
Under the Auth tab you want to specify the private key that putty generated at the way beginning.
That concludes todays write-up! I had a lot of fun with this one. I have used SSH in the past but never configured on my own machines. I hope someone will find some value from this. I also plan to create a video for another reference for others to learn from. As always, Never Stop Learning!