Today we are going to continue our NATAS hack-through. I am really enjoying the Natas wargame.
Level 6
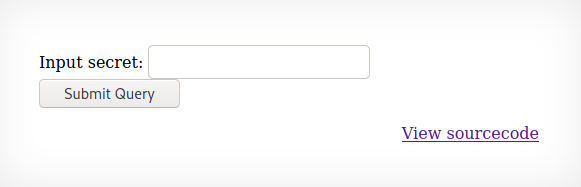
When logging into level 6 we find a form that requests a secret to be entered. It also provides us with the source. This helps us understand what is going on behind the scenes. In a live environment the source code may be hidden or even obfuscated. The point of these wargames are to help familiarize us with different topics and techniques.
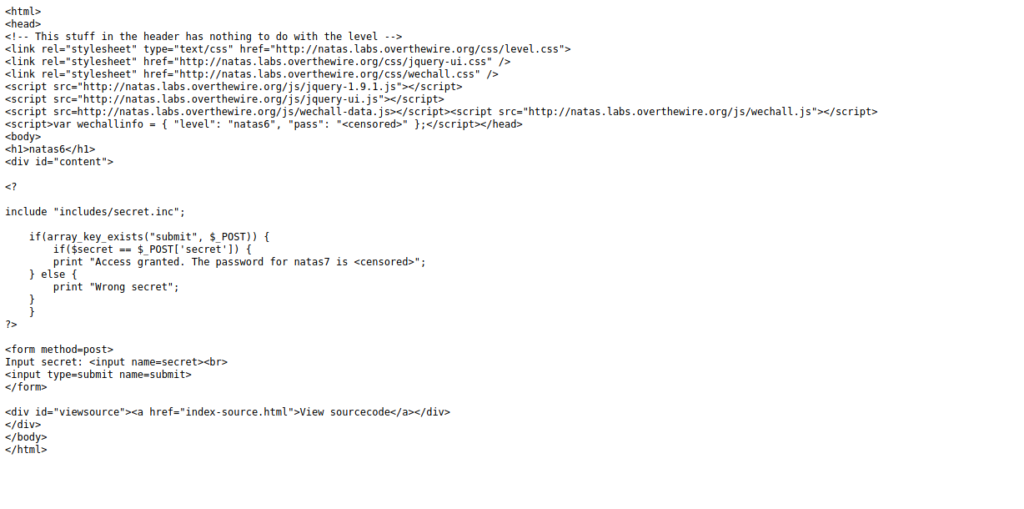
The source code does not contain much. We see a few statements that are looking to match the secret we entered with the $secret variable from secret.inc. Since we can see where this file is located, lets go ahead and see if we have access to it.
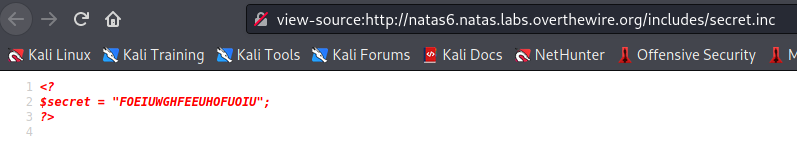
That is it! Not much else was needed on our part. It seems this PHP variable is passed to the form we just took a look at. When we submit this secret we should then get the password to Natas 7.
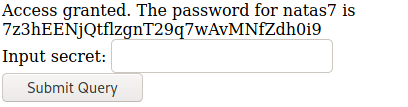
Username: natas7
Password: 7z3hEENjQtflzgnT29q7wAvMNfZdhi0i9
Level 7

When logged into Natas 7 we do not get much aside from two pages. The about page is similar to the home page.
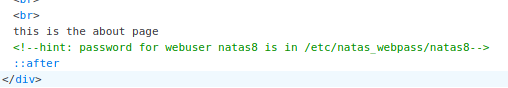
By viewing the source of either page we find a comment. This comment shows us the location of password for Natas 8. (Keep this location in mind as we also use it later in level 9/10). Well since we know this location we can do two things. One we can run up burp, intercept the request and change URL. For this particular case I do not see it necessarily helping or showing us any more than we already know. So with that we can also just try entering it in the URL bar on browser.
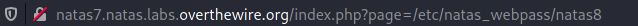
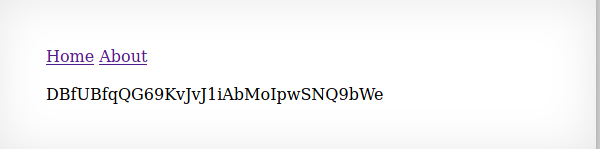
By entering that URL with location page= being set to our hint we are then presented with the password for natas8!
Username: natas8
Password: DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe
Level 8

Level 8, similar to level 6 we are presented with a form that requests a secret to be entered.
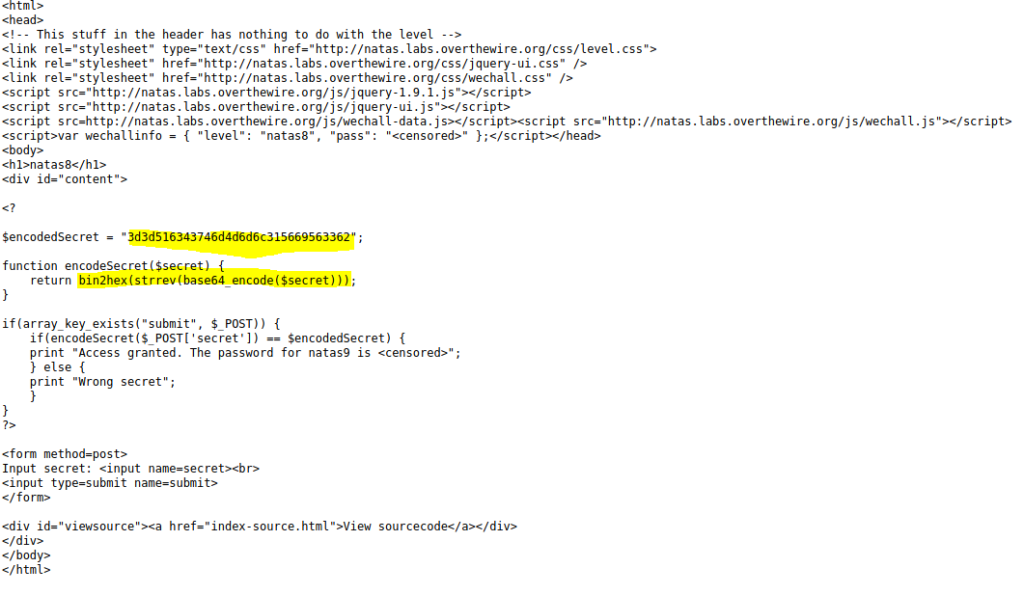
This was one of my favorite levels yet. I have so much to learn going forward but this one in particular I solved without any assistance. I then took a look and found an even cooler approach. One of the biggest reasons why I love cyber. Anyways, lets get back on track. In the source code we notice a some PHP stuff going on. We see a variable named encodedSecret we also see the function that will encrypt or “encode” the string of text given.
Since we have the algorithm to how the encodedSecret was encoded, we can then reverse it. You can do this manually with using tools such as Cyberchef (pretty amazing tool on github). Or you can create a PHP file to just reverse and print to screen.
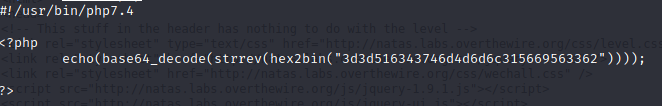
An important takeaway before writing the PHP file is to know which version is installed. You can do this by simply running the php –version command. This will be used for the shebang at the top of the file. If this is incorrect then the file will not know what to run.
Below the shebang is the PHP code. This code is simple. The echo function will print the result of the algorithm inside the () to the screen. Inside we just reversed the source code and instead of entering the variable for user input we just entered the encodedSecret listed from source code.
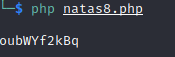
Running the PHP file will print the string to screen.

Entering the string from PHP file into website will display Natas 9 password.
Username: natas9
Password: W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
Level 9
Level 9 and 10 were also two of my favorite so far. I say this because I do not have much experience with command execution just yet. I hear about these security incidents and or vulnerabilities all the time but never get to see it in action. Although this is a simple example I really enjoyed how it came about. This is why it is so important for web developers to ensure security is always in mind.
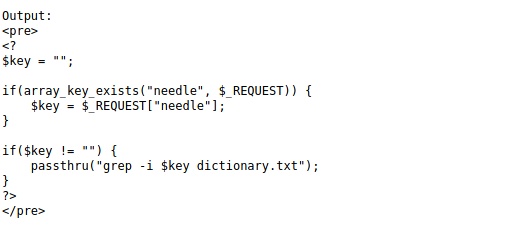
The source code of this level is above. Essentially, the input that we submit will be stored as the $key. This variable will then be used with the grep command. The grep command looks for patterns in files. The -i option allows search to be insensitive to upper or lowercase. followed by the variable and the file we are looking inside.
The part that matters though is the passthru function built into PHP. If not used correctly with user input, it can potentially allow for arbitrary commands to be executed.
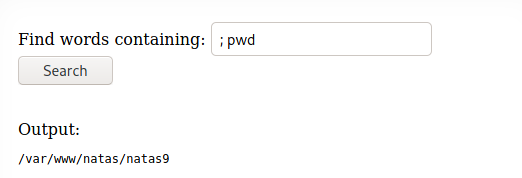
With placing the ; we were able to end previous line, allowing for execution of the pwd command. With no input validation we were able to get the output printed to screen showing current directory the form is working in. As I said earlier since we know where the passwords are stored we can than sneak around with the cd command.
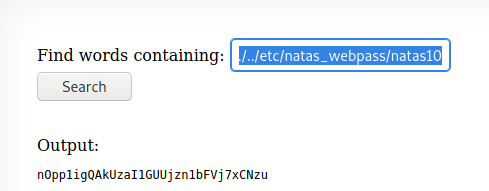
By using ; ls ../../../ I was able to eventually find my way around. Once I found myself in the root directory I Was then able to read /etc/natas_webpass/natas10 by using the cat command.
Username: natas10
Password: n0ppligQAkUzaIlGUUjzn1bFVj7xCNzu
Level 10
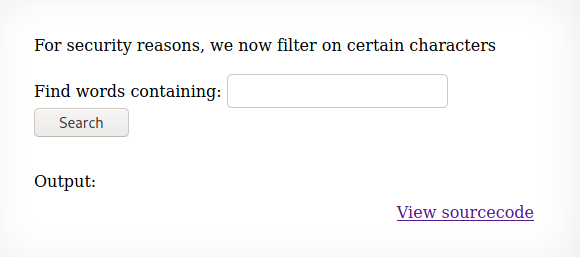
Level 10 is actually quite similar to level 9. The page seems to have updated since last time we used it though because now it filters certain characters.
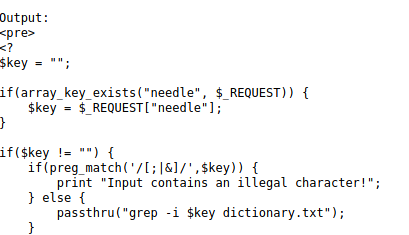
So here we notice nearly all special characters that would benefit us to execute an arbitrary command have been blacklisted. If entering any of these characters a message will tell us that input contains an illegal character!
Instead of taking advantage of the passthru function within PHP, lets take a look at the grep command. In level 9 I explained what was going to happen when we enter some input. It will be stored as the $key and used to search through dictionary.txt. If we look at the man page for grep we see the following:
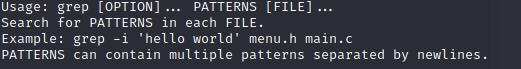
This tells us that we can grep more then one file.
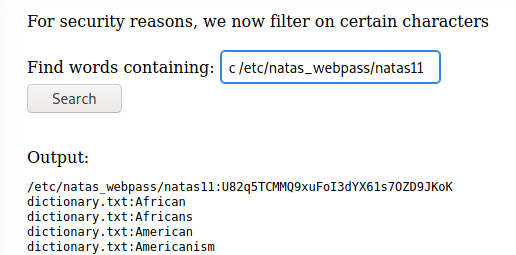
This means that we can search for any letter within the natas11 file and hope it matches. Since c was inside the natas11 file we were able to grep and extract the password for level 11! You could have used the entire alphabet and assumed that eventually a letter or number would show within the pattern and result in a print.
Username: natas11
Password: U82q5TCMMQ9xuFoI3dYX61s70ZD9JKoK
Conclusion
Levels 6-10 are now complete! I have learned a lot this time around. I am really enjoying this format because I am also able to come back around to document what I learned and really reinforce what I learned. I am looking forward to finishing the Natas wargame and onto the next adventure. #NeverStopLearning!