Introduction
Just a few weeks ago Cyber Apocalypse 2022 was being hosted on HackTheBox. Personally, I try to jump into as many of the popular CTF challenges as possible just to gain that required experience. In doing so, I realized I am not used to this style format and needed more practice. Although my goal this year is to focus primarily on the Web side of pen-testing, I found it to be beneficial to start playing in some of the boxes hosted by HTB.
This will be the first instructional write-up for HTB’s Starting Point lab. I am unsure of the format I will use going forward so bare with me. I do plan to not only show the answer but also provide some input to hopefully give you a better understanding of what is going on. While I am doing this I also find myself taking notes of various side-projects I want to get into as well.
Answer: As many of you know by now, VM stands for Virtual Machine. Many of the boxes on HackTheBox will consist of virtual machines hosting various services. An example of this may be an Ubuntu machine hosting an Apache server to deliver a website we are to break into.

Answer: If you did not read the second sentence of this question it could be confusing. Once you see console or shell and think of another term used, you may think of terminal. The terminal is essentially the command prompt on Windows but for Linux machines. I am sure if you are here on HTB then you understand the basic terminology and probably does not need further explanation.

Answer: Although many tools exist to start a VPN session, HTB solely uses OpenVPN.

Answer: The abbreviated name for ‘tunnel interface’ is tun. When starting the VPN connection with OVPN you will see the tun interface being created

This interface would not exist without starting the VPN session. For example if you were to run ifconfig without a VPN session this tunnel would cease to exist. Therefore we would have no communication with the VM hosted by HTB.
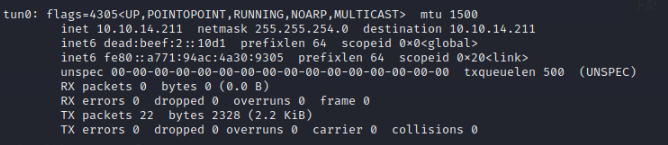
The tun address is also important to know for many reasons but one example would be setting up a reverse shell. If you were to use your local IP subnet for setting up a reverse shell, the connection would drop. This will be displayed over the course of these writeups within Starting Point.
Answer: Internet Control Message Protocol (ICMP) is used for diagnostic/control purposes and response to errors. The tool to test a connection using an ICMP echo request would be ping. Ping is an easy first step to take in troubleshooting network connectivity. Although that is true, make sure you understand many times ping is turned off on the receiving end and would not qualify as a good troubleshooting tool. This is because many malicious attacks will perform reconnaissance and use ping to determine if host is up or down. If the host shows that it is down, that may be enough to divert there attention elsewhere. Especially when bots are at play.
Answer: Nmap is probably in everyone’s toolkit who performs any form of penetration testing or even network troubleshooting. Another great tool I learned recently to gather open ports quickly would be rust. This will also be highlighted in a later walkthrough.

Answer: Well we know nmap is going to be the tool used. Lets take a look at our options
So without any options or scan types, lets specify the target and see what we get

As you can see above, in 13.63 seconds we were able to find our first open port. Port 23 is always a good port to find open when pen-testing. I say that because telnet was not developed with security in mind. Telnet is not encrypted and all traffic is sent over plain-text.
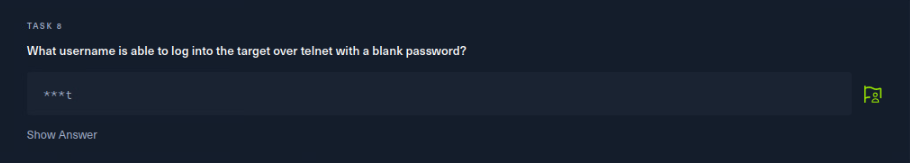
Answer: Aside from guessing what ends in ‘t’ and has four letters, lets think about it from a pen-testing standpoint. If we were to log into any machine and would like to have access to any file, which user would we like to try first? Root. With having access to root we can practically do anything.
In order to use telnet, all we need to do is specify the user (-l) and target (ip address of VM)
telnet -l root <ip address>
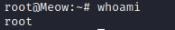
Without even entering a password we now have root access to this machine

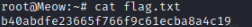
Answer: Now all we have to do is submit the root flag. Generally this will get harder depending on difficulty of machine. In this example all we need to do is list out the contents in the home directory.
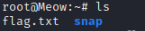
In the home directory we see flag.txt, lets read it using cat
Conclusion
This concludes the first Starting Point lab, Meow! Although much of this information is very basic, I hope I added some value to your learning experience. I plan to document all of the Starting Point labs and continue on thereafter. As always, Never Stop Learning!
