Purpose:
Another day, another write-up! I have completed most of these boxes from HTB a few weeks back. Just now putting some time aside to document the process. Today’s box Fawn, covers some basics of FTP and NMAP scans.
Question:
Answer: File Transfer Protocol
FTP has been around for many years serving as the primary method of transferring files between devices. Ports 20/21 are associated with the FTP service. Similar to Telnet (discussed last week) FTP was not built with security in mind. Easily exploited, as credentials can be sniffed because authentication is sent in clear text. Alternatives to FTP do exist and should be used in almost all scenarios with services exposed to the outside, SFTP and FTPS.
Question:
Answer: Client-Server model
Any machine (does not have to be a physical server) can serve as the FTP server. The client will initiate a request with server. Depending on request being made, the server will either grant or deny.
Question:

Answer: FileZilla
Question:
Answer: 21 TCP
On the server, port 21 will generally be exposed. This is because port 21 is the “Control” and port 20 is used to transfer the data if granted.
Question:
Answer: SFTP
Secure Shell File Transfer Protocol (SFTP) is essentially FTP but with SSH components built in. No longer is authentication sent over plain text, instead all transmissions are now encrypted. With encryption being used the information can no longer be sniffed. Another difference is the ports used. Instead of 20/21, SFTP will utilize port 22.
Question:
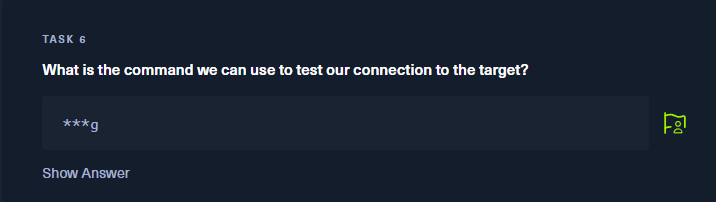
Answer: Ping
Question:
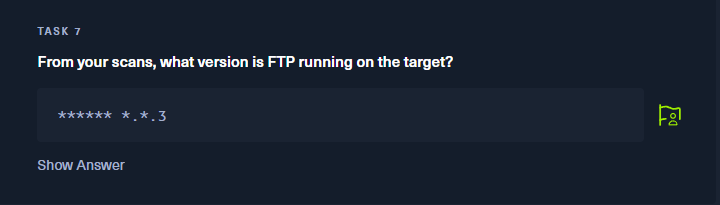
Answer: vsftpd 3.0.3
In order for us to determine the version lets do some recon on the system. First with a basic NMAP scan to see which ports are exposed.
nmap <ip_address>
Now that we verified port 21 is open, lets use -sV option in NMAP to determine the verision of service. We can also use -A.

We now see the FTP version all the way to the right of result. Often times this is used to help find vulnerabilities. We can then do searches on Google to find existing vulnerabilities and try to exploit that way.
Question:

Answer: Unix
We can also see this from last NMAP scan at the very bottom listed as ‘Service Info’
Question:

Answer: 035db21c881520061c53e0536e44f815
At this point all we know is we have an FTP service open on port 21. We also know the version number and can find a known vulnerability (CVE-2015-1419) but instead, its always best to start with the basics. Performing effective reconnaissance is critical to ones success in finding a way in. With the -sV option we found the version and OS type. Lets take it a step further and find out everything we can about port 21 on this IP address
nmap -A <ip address> -p 21
From this scan, two things stand out. First, we notice ‘Anonymous FTP login allowed’ and we also see a file ‘flag.txt’. In doing some research, you will find that with Anonymous login enabled users can essentially login without any form of authentication. It is astonishing that organizations today still fall victim to such an attack, especially in one with sensitive data such as Hospitals and the alike.
With that in mind, lets try logging in with Anonymous

As you can see above, I was able to login with anonymous and no password was required. From here lets look for that flag.txt file mentioned earlier using the command dir or ls.

Now lets look up what options are available to us using command ?
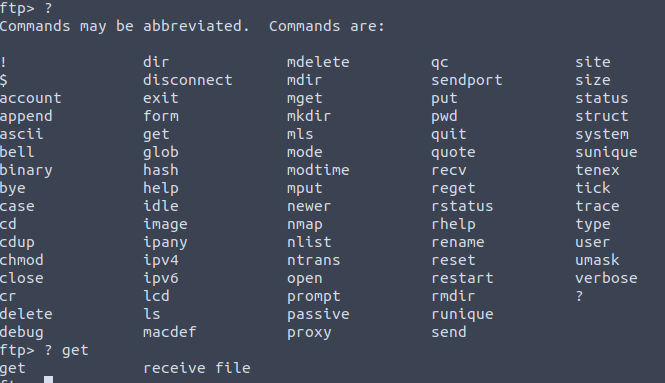
Now that we have all available options, lets use ? to learn more about the command. You will notice that ‘? get’ tells us that we can receive file.
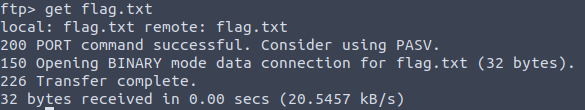
This will download the flag to current directory prior to entering FTP session.
Conclusion
Today’s write up covered FTP and NMAP. Biggest takeaway aside from how to perform these steps is to remember to start with the basics. Often times a vulnerability does exist and it can be something so simple such as default username/password. Or as in today’s case, anonymous login was enabled. While doing these labs, take note of these actions to add to the toolbox later on for your own attacks.
As always, Never Stop Learning!
