I took off of learning anything other then topics related to Security+ for the last several months. I had a goal day for September 20th to become certified. As of September 4th I am now Security+ certified! Super excited to continue on with this journey. So with that being said it is back to the lab.
Todays adventure will cover an experience recently I had with file-sharing over a home network. I was testing out an Access database I developed for a business on my laptop. One of their requests was to have it shared between their home network. I wanted to deploy everything on my own network to ensure everything would work as I envisioned.
Problem: A mapped folder on home PC was not able to be seen on laptop.
I started out with verifying file sharing settings on both computers.

Only focusing on the “Private” settings considering location of files and my intentions. I then considered that maybe the connection to the network is improperly configured and is not showing as private thus blocking the connection.

I try to use Powershell as much as possible considering how powerful it is. With the “Get-NetConnectionProfile” I was able to determine if both devices had the same category as “Private”. Well the laptop was showing otherwise. I then went ahead and changed the category using the following command.
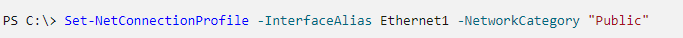
Now with both using the same category I thought I fixed it. I was wrong, nothing changed. An easy process I tend to follow with network related problems especially on my home network is to rule out the firewall. So next I disabled the firewall on my PC which is sharing the folder. I immediately was able to find the folder on other device. Now I know where to start. I turned firewall back on and headed into the rules. I assumed it was an incoming rule blocking the connection. Still learning, I was unsure of exactly what port was being used for this share so I was just manually scrolling through.

All inbound rules relating to “File and Printer Sharing”. I did not see anything out of the ordinary here. Even tried making a rule to allow all inbound SMB connections over 445 but nothing changed. So then I learned about the ability to enable logging for firewall.


After turning on “Log dropped packets” I was immediately able to see what exactly was going on when I would attempt to map the drive on laptop. It was a rule blocking port 445. To my knowledge I viewed all rules relating to 445 with the picture posted above. Again I was wrong. This is where I messed up. A few months ago when playing around and understanding the various vulnerabilities related to file sharing I went ahead and just made a custom rule to block all inbound traffic over port 445. I was only able to notice this after filtering the rules specifically looking for this port.

“TestBlock” was the custom rule I implemented to see it in action. Once I disabled this rule, everything worked as I intended.
The biggest takeaway here for me was the ability to log firewall information. Without logging I may have been chasing my tail for a bit longer. It was a lot easier to focus on the problem when it explicitly told me that inbound laptop “ip” “port anything” was blocked on home pc “ip” “port 445.”
I think that is enough for todays writeup. As always NeverStopLearning!