Today we are going to take a look at the NATAS games over at OverTheWire.org. My motivation to start with the NATAS games was to learn and freshen up on some web hacking. I am looking to build a better base for when I go into these various CTF challenges and continue my journey into Cyber.
Level 0
In order to start these challenges head on over to overthewire.org. Once there on the left hand side you will see a menu consisting off all the Wargames OTW has to offer. Each having its purpose. Natas focuses on the web side of things. The first few levels are pretty straight forward. Minor details along with the picture should be enough explanation.
Like Most beginner challenges they force you to look at the source code. This is important as we must get familiar with HTML and its various components in order to understand how it all works and how to break it. You can do this by right click > view source code.
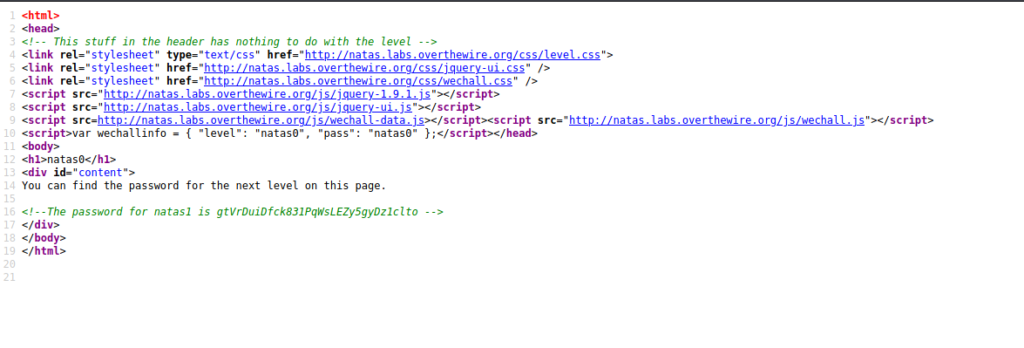
Easy enough! As you can see the notes annotated with a <!– –> display the password for the next level within natas. In order to connect all that we are required to do is replace the URL with natas1 instead of natas0. It will then request a username and password.
Username: natas1
Password: gtVrDuiDfck831PqWsLEZy5gyDz1clto
Level 1
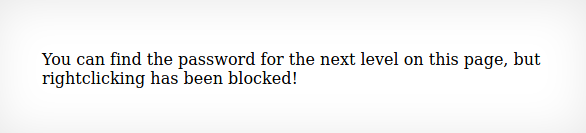
Once logged in you will be notified that you can not right-click and view source anymore. Well another method we can use today is with depressing our F12 key. This will bring up another screen allowing us to view the source.
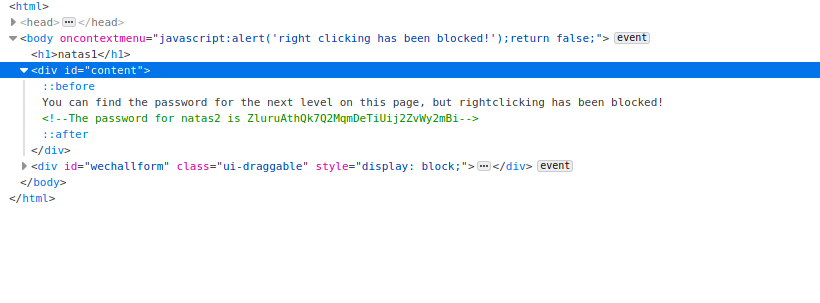
Here we can see the password for Natas2 again within a note in html format
Username: natas2
Password: sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
Level 2
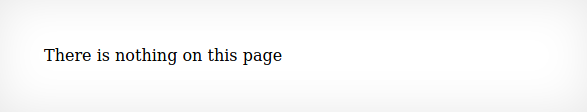
Natas2 will tell us nothing is on this page. Lets take another look at the source code.
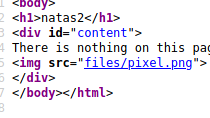
This time their was no giveaway for the flag within a comment. Instead we noticed a new image and directory being introduced. Instead of going to the /files/pixel.png location lets check out /files first.
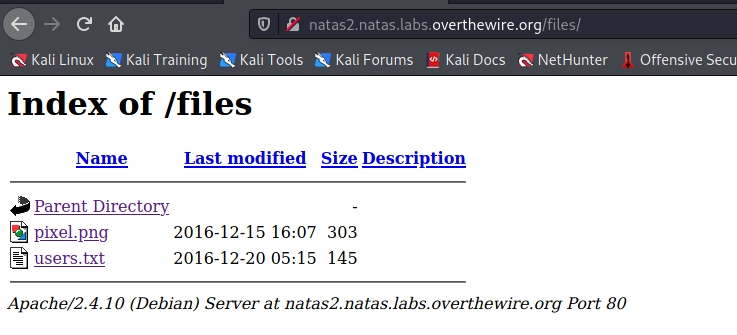
This looks promising! Lets open up the users text file.
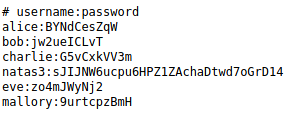
We now have the information needed to login to Natas3.
Username: Natas3
Password: Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 3
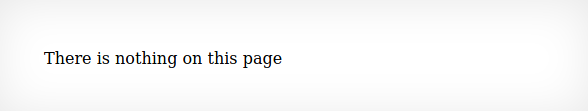
Similar to Natas2 we are being told nothing is here.
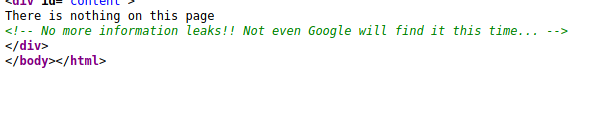
In the source code we could not find the password. Instead we noticed a comment that says no more leaks! Also mentions something about Google not being able to find it this time. Without an understanding of why Google may play a part this may be challenging. These search engines can use a specific file given by the developer in order to tell what URL the crawler can access. This file is called the robots.txt file. This was the first spot I checked and was correct.
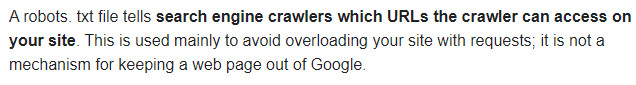
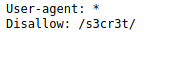
When heading over to the robots.txt location we noticed that a directory /s3cr3t/ may or may not exist. Lets take a look.
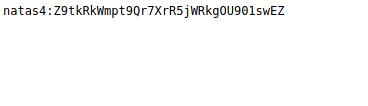
When opening up this directory in Firefox we were given the password for natas4.
Username: Natas4
Password: iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
Level 4
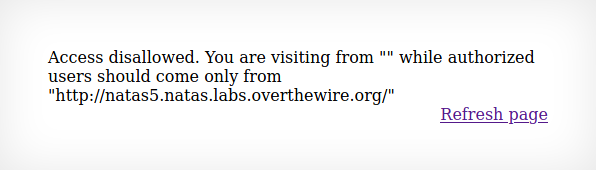
This is when it starts getting fun! One of my favorite tools, Burp Suite. If not familiar with Burp, it is an application we can use to have a closer look at what is going on behind the scenes. Allowing us to view the data being passed from client to the server and its return. Also allows us to modify the data being sent. Essentially Natas4 is saying that in order to view this site we would need to be coming from natas5. Obviously this is not possible as we do not have the password to login to natas5 (yet). What we can do though is tell the server that this is where we came from.
side-note: Got the FoxyProxy going :). For the longest time I would use the built in browser within Burp. I have said for a few months that I would switch over and so far I am loving it. Just a convenience factor.
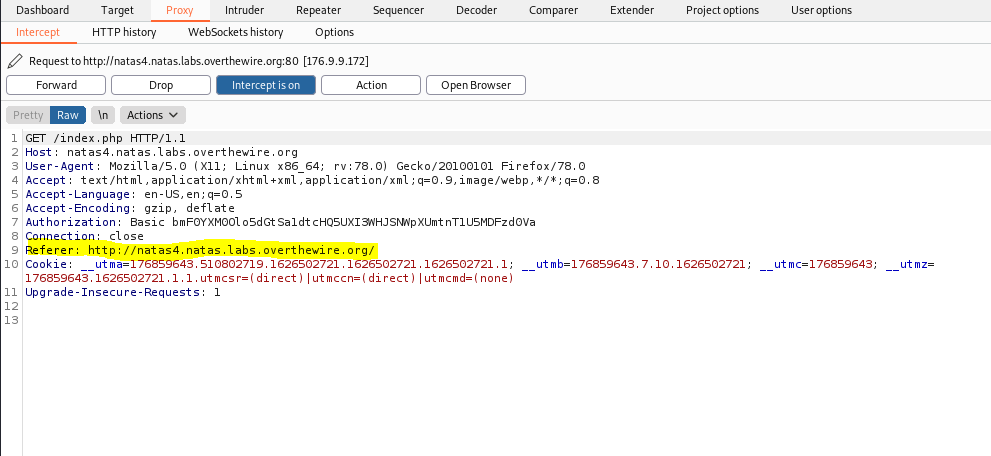
After setting up burp and turning on the intercept option under proxy we will first refresh the page. Doing so will then send the information to Burp. As you can see highlighted, all we would need to change is the “referrer” to the one that is being requested.
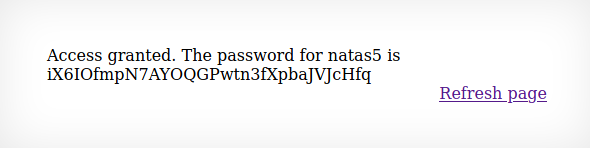
After changing the value of the referrer we would then be granted access and given the password for natas5.
Username: natas5
Password: iX6I0fmpN7AY0QGPwtn3fXpbaJVJcHfq
Level 5

Similar technique is used for Natas5. Get the burp going and lets see what we get.
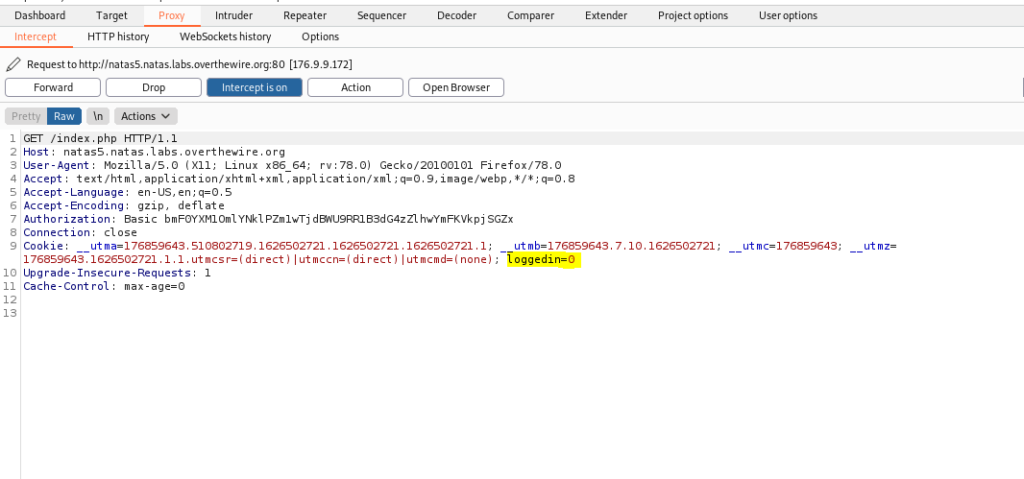
Here we noticed a loggedin=0. Well what happens if we change it from a 0 to 1 or otherwise known as false to true?
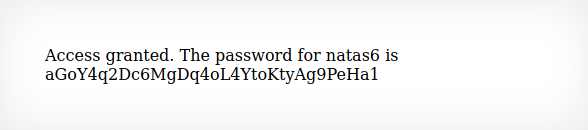
Access Granted!
Conclusion
This ends today’s writeup for levels 0-5. Next we will go even further and have some more fun within the Natas Wargame. As always #NeverStopLearning!!