Disclaimer: I know after our last post we said we would cover a weekend project I had accomplished in regards to creating/hosting our very own docker container. Although I do still plan to cover this I had recently been deep in the lab (on the road) learning more about CISCO networking. I have been enjoying Packet Tracer so much that I thought it would be a great post discussing some basic concepts.
Purpose: For this lab we are going to act as if we are creating an entire network for this company. After discussing the details with the owner we decided the three departments (Nerds, Staff, Users) are going to not only physically seperated but also logically separated using three VLANs. Although each device will be placed in its own VLAN we still want to allow communication between the three networks using routing on a L3 switch. We will also enable SSH for the the Nerds subnet into the L3 switch. Allowing them to remotely administer the switch instead of having to plug directly into the switch.
So in this lab we will cover initial configuration of a switch, we will create three networks within different subnets/VLANs. Lastly we will cover enabling SSH and creating an ACL only allowing a specific subnet to have SSH access.
Diagram:
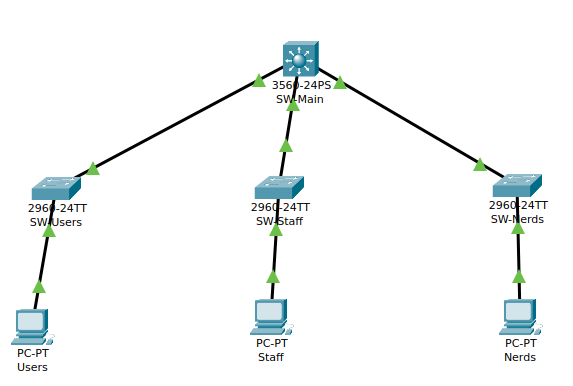
Note: We are just using one computer for each network to cover the concept. Obviously in a real environment many computers will be present and the configuration may look a bit different. With that being said as you can see we have three computers all connecting to its own layer 2 switch (2690). This would again vary depending on the network layout/topology.
Network segmentation
| Name | IP | CIDR |
| SW-Main | 10.0.10.1, 10.0.10.33, 10.0.10.65 | /27 |
| Users (vlan 40) | 10.0.10.40 | /27 |
| Staff (vlan 70) | 10.0.10.70 | /27 |
| Nerds (vlan 10) | 10.0.10.10 | /27 |
As you can see we split the network up into three networks essentially.
10.0.10.0-10.0.10.31 will be used for Nerds and other Nerd devices including L3 switch
10.0.10.32-10.0.10.63 will be used for Users computers
10.0.10.64-10.0.10.95 will be used for staff computers
Even if all computers were in same VLAN but split into different subnets they would not be able to talk to each other without layer 3 routing.
Configure IP settings for Computers
Instead of covering the same instructions three times for the three computers shown on diagram, we are going to cover one and expect the rest to be common sense.
- Click on the computer
2. Click on config
3. Under global settings define default gateway and set to 10.0.10.1 (IP address for SW-Main VLAN 10 explained later)
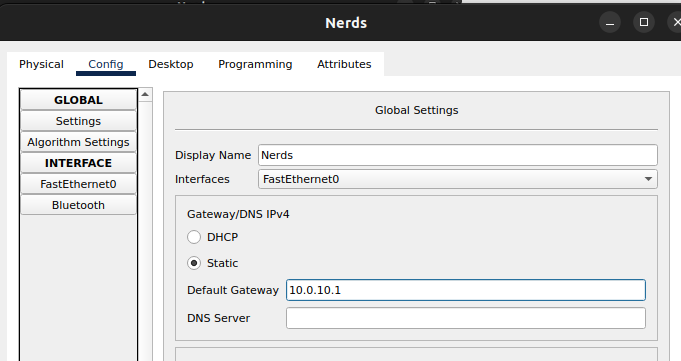
4. Click on the FastEthernet0 INTERFACE tab
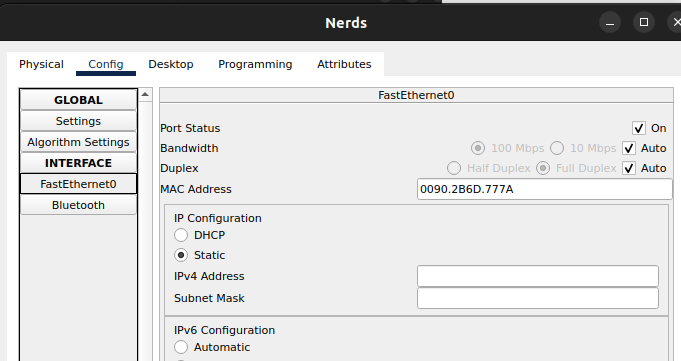
5. Define the IP configurations for IPv4 (Address/Mask)
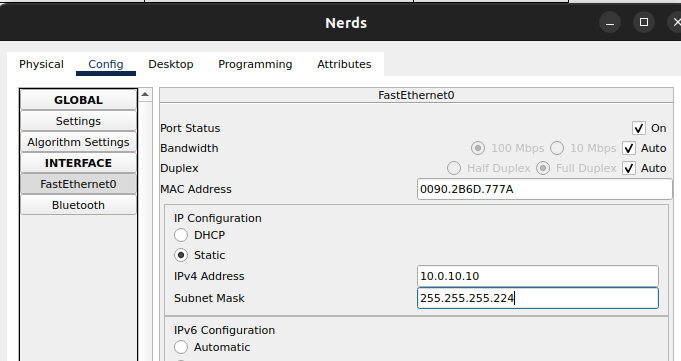
Note: The Subnet Mask for /27 is 255.255.255.224
Do this for all three machines before moving on.
Initial configuration of switch
In this step we will cover briefly on how to set secrets for the initial login and enable (privileged)
- Create line console password
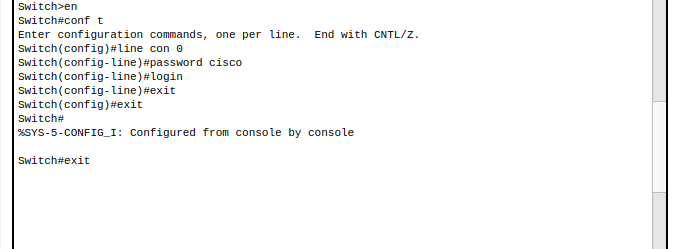
2. Test password by exiting enable mode

3. Create enable secret
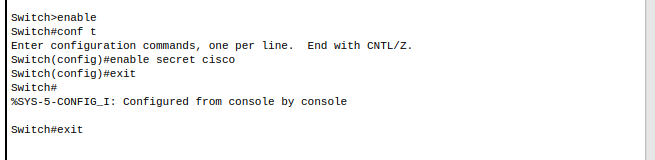
4. Test enable secret

5. View running-config
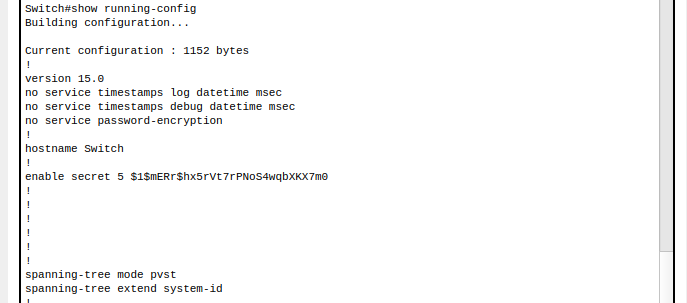

Here you can see that in our running-config we have a secret for enable and a password for line console. For better practice lets go ahead and change one more configuration on our running-config in order to encrypt all clear text passwords.
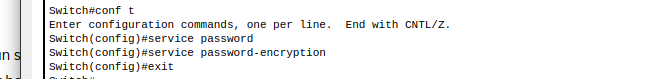
In configuration terminal we set service password-encryption. By default this is set to ‘no service password-encryption’

Note: Although this encryption is reversible it is still better practice then storing in clear text. The biggest difference here is that we were able to store our enable password as a secret which is a hashed value and would require brute force to gain access (not reversible).
You can do this for the remaining switches if you would like or just do one for practice.
Create VLANs and assign interfaces (Layer 2)
- Create VLAN for nerds
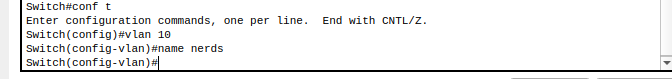
2. Verify connected port/interface using ‘show interface status’
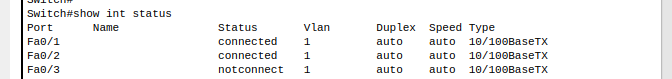
3. Assign interface (port 2) connected to nerds computer to VLAN 10
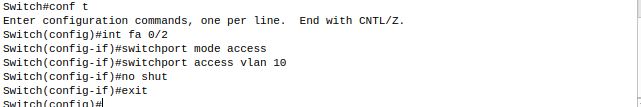
4. Verify interface is assigned to VLAN 10 using ‘show int status’
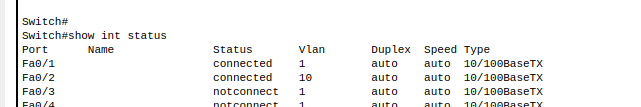
5. Ensure state of VLAN 10 is up
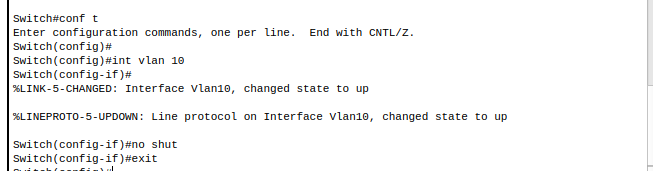
Do this for each of the switches. Assign the devices which are connected to port 2 on the layer 2 switches to their associated VLAN as shown earlier in table.
Trunking Layer 2
In order for Inter-VLAN communication to take place we must send the traffic over what is called the trunk port. This will be required for whatever port is connected to the Layer 3 switch. In our case 0/1.
- Change mode of fa 0/1 on layer 2 switch to trunk
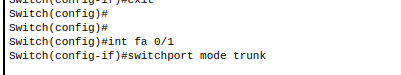
2. Verify interface status
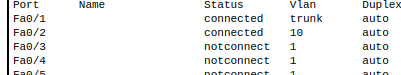
Do this for the other two switches as well.
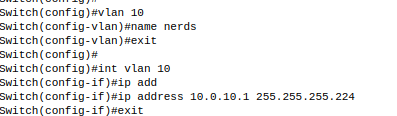
Create VLANs on Layer 3 and assign IP address
- Create VLAN and assign IP address
2. Test ping from computer to gateway 10.0.10.1
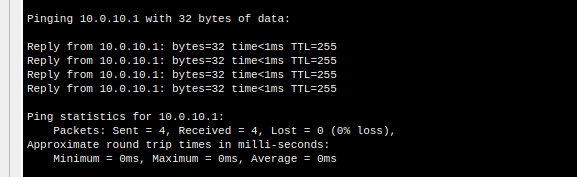
Do this for the other VLANs as well (40/70), make sure you are using the same subnet to ensure connectivity between machine and gateway.
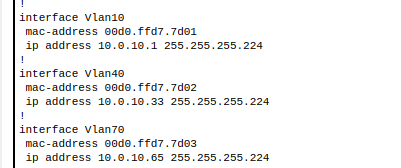
Ensure those IP addresses are configured correctly on each of the computers connected. This was covered under the first section ‘Network Segmentation’ and configuring the individual IP addresses for each machine. Ensure that the gateways on those various L2 networks have the correct gateway associated with that VLAN.
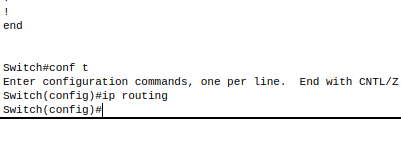
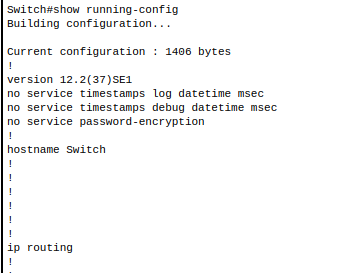
Enable ip routing (Layer 3 switch)
- Enable ip routing for configuration
Save running configuration
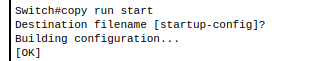
Note: If you do not save the running-config to overwrite the startup-config you will have lost all progress after rebooting the switch.
- Copy running-config startup-config
Enable SSH on SW-Main (Layer 3)
- Assign IP domain name to SW-Main
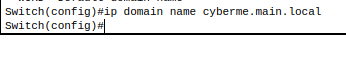
2. Assign hostname for switch
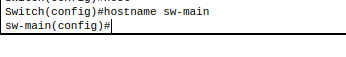
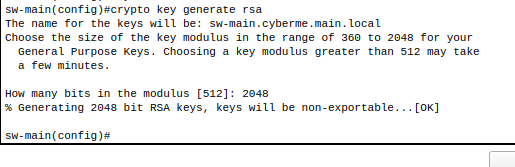
3. Generate RSA Key, 2048
4. Create username/secret

5. Define SSH version and prevent any other connection other then SSH
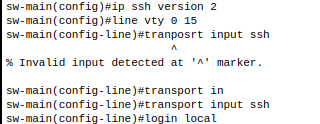
Note: Also use login local for configuration allowing us to login using the credentials defined in step 4
6. Test SSH from computer
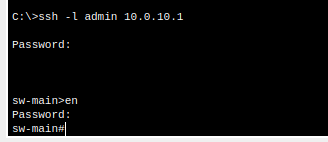
Note: SSH works! The problem is that we can SSH into the switch from any subnet including users/staff. Lets change this using ACL’s.
ACL to limit SSH access to nerds subnet
- Create ACL
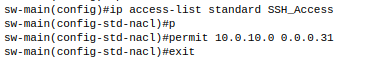
Note: Do not use the 255.255.255.224, I started typing before realizing what I was doing. Must be 0.0.0.31 (wildcard mask)
2. Assign that ACL to running configuration vty line 0 15
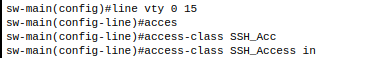
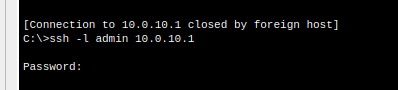
3. Test on nerds subnet
4. Test on either staff or users subnet
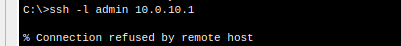
We now have limited SSH Access to only those who need it on the nerds subnet.
Conclusion
As I said earlier I am really enjoying learning more about administering a CISCO network. I am fairly new to this side of the house but I feel as if I am picking it up fairly quickly. I do not plan to go after the CCNA at this time but maybe in the future it is a possibility. I am just trying to sharpen my overall skill set and later on dive deeper and maybe get certified in whatever it is that I decide I am more passionate about.
I hope this instructional post was easy to follow for those who are interested. You can learn a lot from following this lab. I did not cover the basics on how or why certain things are the way they are. Instead I wanted to cover strictly those concepts explained above and the steps involved. Later this month I plan to cover port-security, automating backup of configuration files, DHCP broadcast and a few other things that I find important.
Until then, Never Stop Learning!