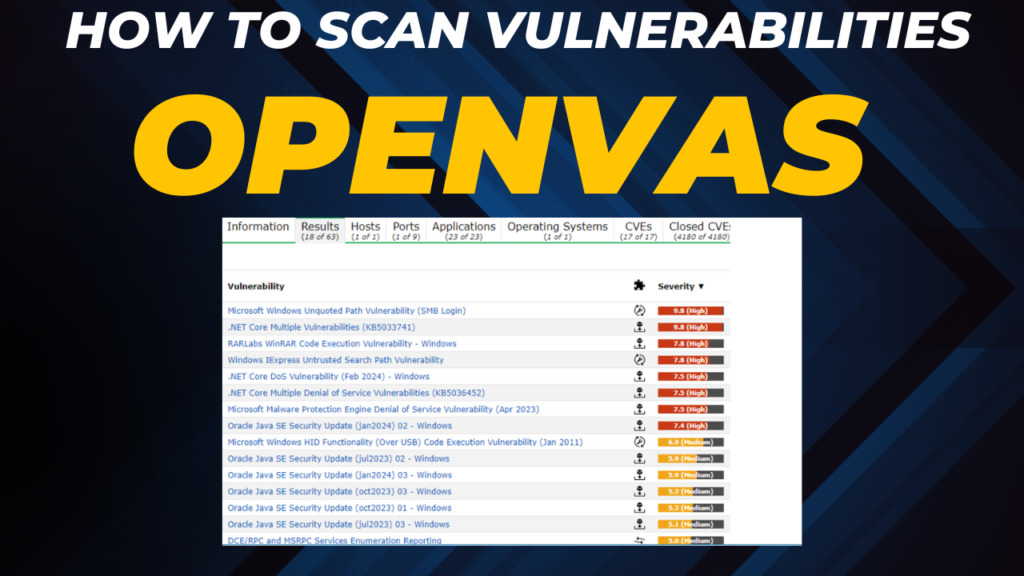
Purpose:
How can you secure the network if you do not know what is vulnerable? There are measures that can be put in place to harden the network and each of the endpoints, but it is equally just as important to stay up to date with vulnerabilities and making sure that everything is patched and up to date. This would not cover for the times where a device is affected by a zero-day and no plugin but most times a critical vulnerability that led to a breach was left unpatched for days, and in most cases months!
Using OpenVAS we are going to scan our test device for vulnerabilities. We are going to walk through the process of setting up a scan after a fresh install. If you have not installed OpenVAS (GreenBone) be sure to check out our blog from last week (blog) or watch the video over on our YouTube channel (Video).
Step 1 – Updating OpenVAS vulnerability feeds:
It is important that we update our feeds before running any vulnerability scan. If the database or feed is not updated we will miss vulnerabilities that do exist but are not being checked. Easy enough, Greenbone provides the commands for us to use. We can then place this in a bash script, schedule with cronjob at night. This way every night our images/containers are updated with the latest image ready for the following day.
All previous data is stored in the volumes defined by the .yml file can be found in /var/lib/docker/volumes
docker-compose -f docker-compose.yml pull notus-data vulnerability-tests scap-data dfn-cert-data cert-bund-data report-formats data-objects
docker-compose -f docker-compose.yml up -d notus-data vulnerability-tests scap-data dfn-cert-data cert-bund-data report-formats data-objects
Step 2 – Setting up credentials for a authenticated scan
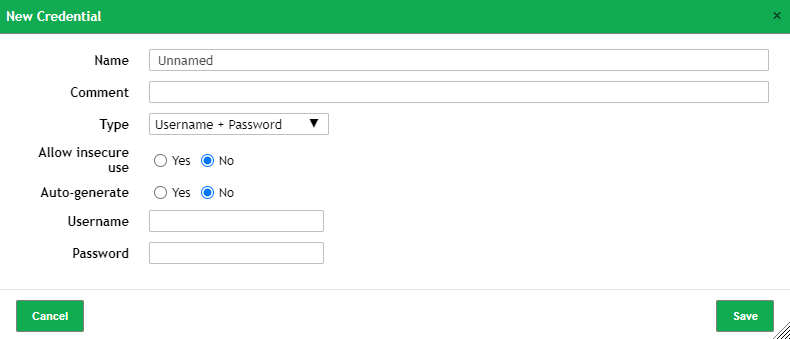
Under configuration, click ‘Credentials’
Look to the top left of dashboard and click the ‘New Credential‘ icon
In the ‘New Credential’ form
- Name : Label used for identifying which credential it is after being saved
- Type : Username + Password, will be used for SMB authentication later on
- Allow insecure use : ‘No’
- Auto-generate : ‘No’
- Username : Username used to login to scanned device
- Password : Password used to login to scanned device
Step 3 – Network Discovery used to determine live hosts
For this lab this it is not necessary but in most cases this can be used to discover all hosts on the network. Lets say you have a network space of 192.168.0.0/16. If you were to run a scan everyday against all of these addresses but only a select few are online, you are potentially wasting network resources and time. Performing a network discovery can help determine what hosts are online and what should be scanned.
Under the ‘Configuration’ tab click ‘Targets’
Top left of screen click ‘New Target’

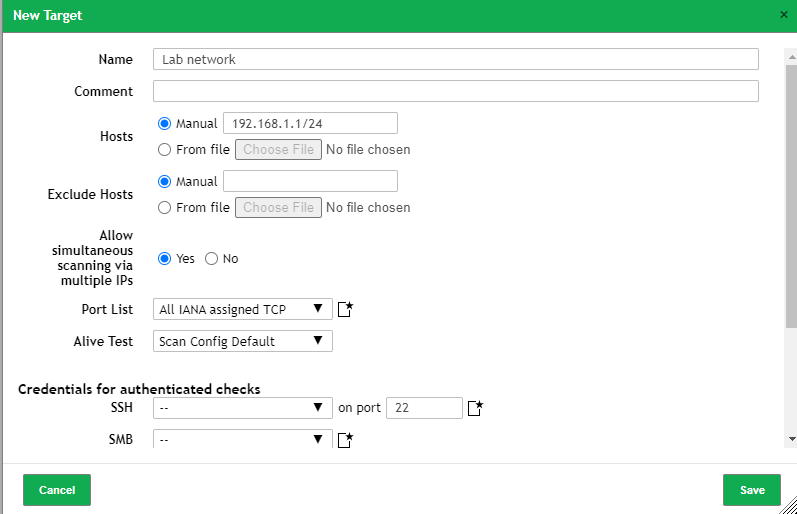
Fill in the following fields:
- Name
- Hosts : Manual, type in address space. In this example I used the address 192.168.1.1 with /24 CIDR notation in order to capture all 254 hosts within this space
- Everything else default
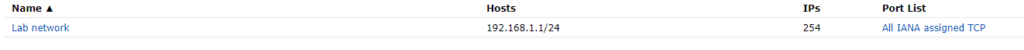
Verify target created
Under the ‘Scans’ tab click ‘Tasks’
Top left of screen again click on ‘New Task’
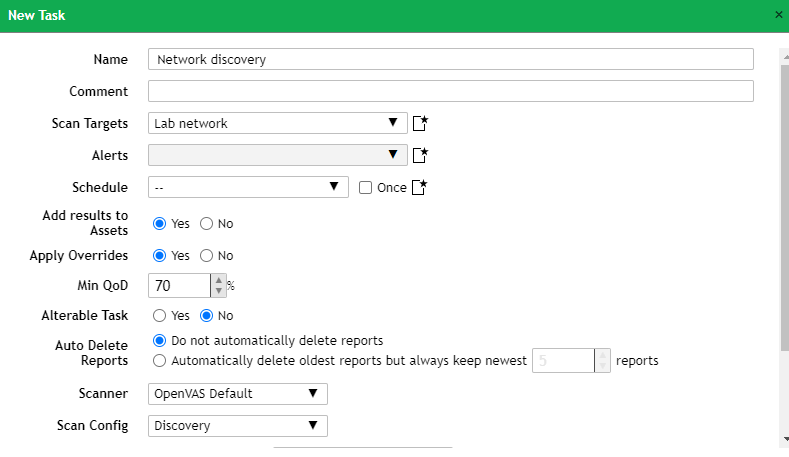
Fill out the following fields:
- Name
- Scan Targets : Select the ‘Lab network’ target we created
- Scan config : Select ‘Discovery’
Verify scan created and click start

The scan may take some time but once it is complete, head over to the ‘Assets’ tab and click ‘Hosts’
You will notice in this tab the hosts found in the defined network
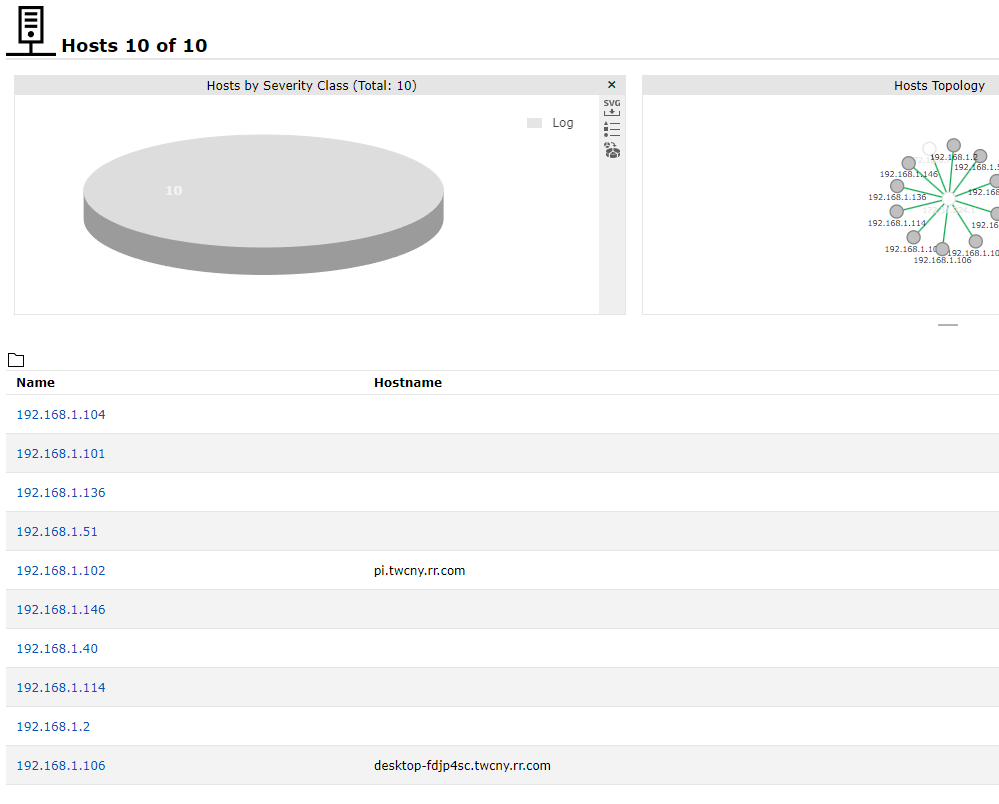
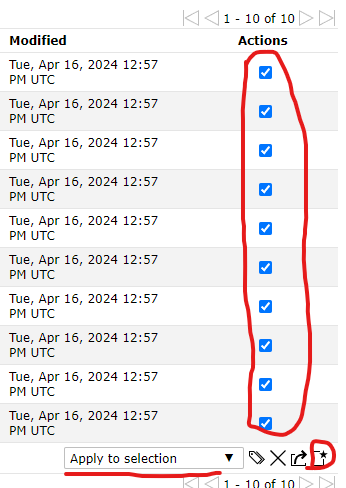
Now that we have a list of hosts on our network we can create a target list from these hosts to be later used in a scan.
At the bottom right of this page select the drop down list and click ‘Apply to selection’. You will then select any number of hosts you would like to add to a target followed by clicking on the icon at the bottom right to create a target from selected assets.
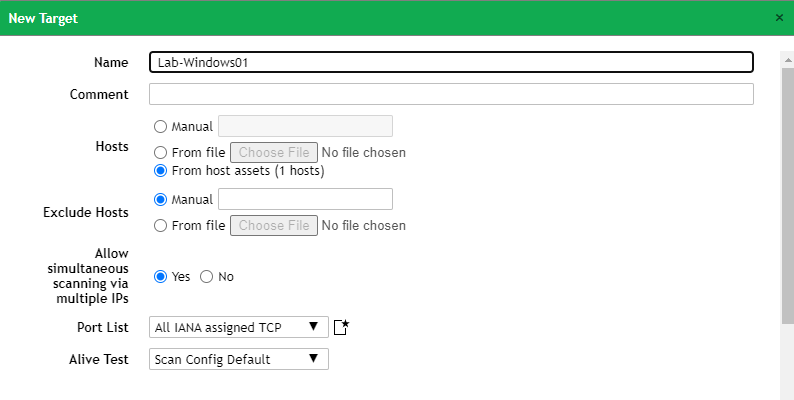
Step 4 – Defining target with credentials
From the previous step, after clicking on the icon you will be presented with a new screen allowing you to define the target and even create a credential.
To start, type in a name for the target
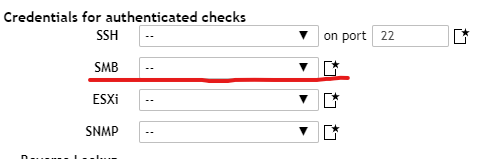
Scroll down until you see ‘SMB’. Here is where you will assign a credential for this target. If you do not have one created (we have not created one yet) you can select the icon to the right of SMB dropdown
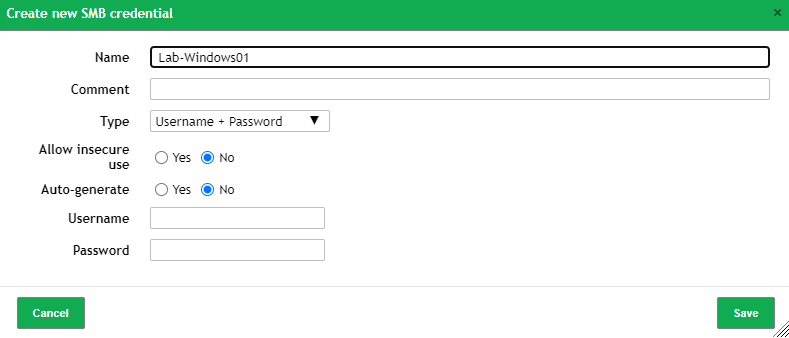
This will bring up another screen allowing you to fill out the information. Pretty straight forward. Fill out the name, username/password and save
After you click save you will be brought to the target page displaying the target we had just created.
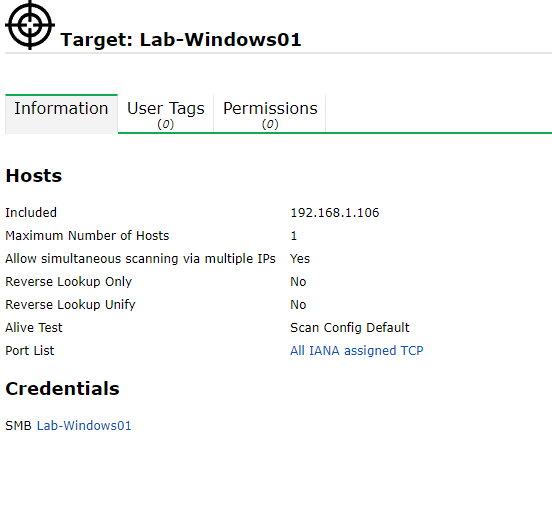
Step 5 – Scanning for vulnerabilities
At this point we have scanned the entire network for hosts. We found a select few we would like to scan. We have exported these hosts into a target file and defined the correct credentials. All that is left now is to set up a scan and let it run.
Click on ‘Tasks’ under the ‘Scans’ tab
Top left of screen click on ‘New Task’
We are going to be using the default scan configurations but in the future we can go into detail about setting up a custom scan configuration.
Once the new task window appears, fill out the Name and Scan Targets. The scan targets will be the target we had just defined. At this point just verify Scan Config is defaulted to Full and Fast and click save
You will now notice that another scan has been created under the network discover scan we had previously created. Click the ‘play’ button to the right of that task and let it run

Step 6 – Reviewing results
Under the ‘Tasks’ page where we ran the scan you will click the ‘1’ under ‘Reports’ column
You will find the summary of scan and since it is currently still in progress you will get the current status

If you click on the date it will bring you to the results page for this particular scan
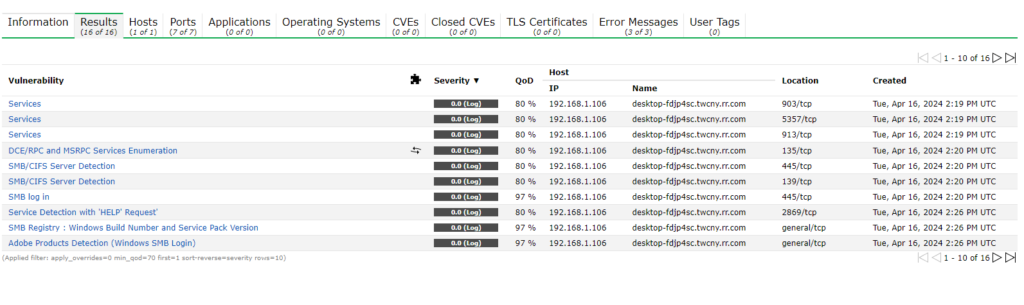
Once it is complete you can view the final results by refreshing this page or coming back later on. As you can see for my lab machine we got some work…
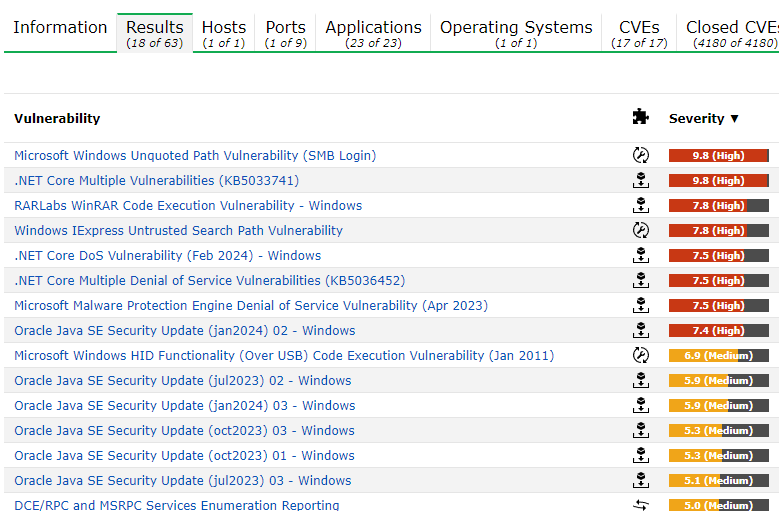
Conclusion
In this walkthrough we covered how to scan our network for vulnerabilities. We first started off with ensuring our vulnerability database if updated. If the database is not updated we may miss out on finding current vulnerabilities. Once updated, we scanned our network to discover which assets exists and which are alive. From there we were able to create a target list and perform a credentialed scan.
I hope you were able to take something away from this walkthrough. If any questions are left, please feel free to drop a comment below or head over to the YouTube channel and reach out. I do my best to respond to questions in a timely manner.
As always, Never Stop Learning!